Contributed by coRAN Labs (CRL)
The 5G evolution is accelerating, unlocking new capabilities across every sector of the global economy. But this progress comes with an equally rapid expansion of the threat landscape. Among the most disruptive risks on the horizon is the rise of quantum computing, which directly threatens today’s cryptographic foundations and, by extension, the security of 5G networks.
At coRAN Labs, we are addressing this challenge head-on by integrating Post-Quantum Cryptography (PQC) into open, cloud-native 5G cores starting with Aether SD-Core. In this blog, we introduce QORE, our Quantum-Secure Aether SD-Core architecture, and show how open ecosystems like Aether can lead the way toward quantum-resilient telecom infrastructure.
The Quantum Threat to Today’s Cryptography
Quantum computing poses an imminent threat to classical security mechanisms, especially asymmetric cryptographic primitives based on the Elliptic Curve Discrete Logarithm Problem (ECDLP) and RSA. Asymmetric cryptography underpins modern network security: it enables secure key exchange for symmetric algorithms such as AES and ChaCha, and is deeply embedded in protocols like TLS/DTLS, IPsec, and more.
A Cryptographically Relevant Quantum Computer (CRQC) capable of executing Shor’s algorithm would efficiently solve the underlying hard problems of these schemes, rendering them insecure.
Two attack models are particularly concerning:
- Harvest Now, Decrypt Later (HNDL) – Adversaries record encrypted traffic today with the intention of decrypting it once CRQCs become available. Even passive adversaries can eventually break the confidentiality of sensitive traffic, including critical infrastructure data that must remain secret for years or decades.
- Trust Now, Forge Later – Adversaries can later forge digital signatures, undermining PKI and breaking the trust model for everything from software updates to banking operations.
Active adversaries with access to a CRQC (in the future) would be able to decrypt and forge ongoing communications secured by classical cryptography, leading to man-in-the-middle attacks, impersonation, large-scale data breaches, loss of integrity, and denial-of-service at a systemic level.
Securing 5G Against Quantum Threats with Post-Quantum Cryptography
Given the inevitability of quantum-enabled attacks on conventional cryptography, migrating to Post-Quantum (PQ) methods is no longer optional it is urgent. 5G is a particularly critical target: it carries highly sensitive subscriber data, control-plane signaling, and network configuration. Security failures in 5G can have severe consequences, including:
- Certificate forgery – Malicious entities can insert themselves into trust chains, disrupt services, and undermine network trust.
- Key leakage – Exposure of long-term or session keys allows attackers to intercept, manipulate, or block traffic.
- Authorization failures – In 5G Core Service-Based Architecture (SBA), a broken OAuth flow could let an attacker:
- Access UE data
- Manipulate QoS parameters
- Disrupt control plane signaling
- Compromise 5G-AKA and SEAF keys
- Alter network slice profiles, policies, and rules
The risks posed by quantum computers are too broad and long-lived to ignore. 5G security must evolve toward quantum-safety. In this blog, we describe how we integrate NIST-standardized PQ primitives ML-KEM and ML-DSA into open 5G cores, and how we upgrade:
- TLS & OAuth 2.0 on Service-Based Interfaces (SBI) to PQ-TLS 1.3 and PQ-O Auth 2.0
- gNB-Core interfaces (NGAP & N3) using PQ-IKEv2 for future-proof tunnel protection
Our solution is implemented in open source 5G cores such as Aether SD-Core and free5GC. QORE has been validated with our Q-RAN enhancements, demonstrating robust quantum-safe integration and future-ready interoperability between next-generation 5G Core and RAN components under advanced PQ security standards.
QORE as a Bridge Between Standards and Quantum-Safe 5G Deployment
Telecommunication networks especially 5G Core and RAN have long lifecycles and handle mission-critical, privacy-sensitive data. This makes them prime targets for harvest-now-decrypt-later attacks, where adversaries store encrypted traffic today with the aim of decrypting it in the post-quantum era.
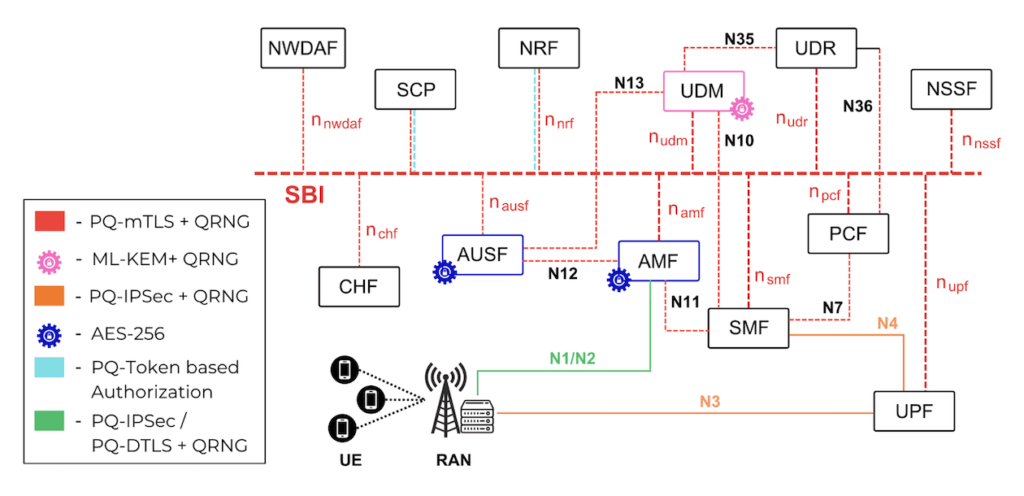
Figure: QORE – Post-Quantum Secure 5G Core Architecture
To ensure long-term confidentiality and trust, operators must start phased PQ migration now, guided by open standards and interoperable reference implementations. At coRAN Labs, our Post Quantum upgrade strategy for Aether SD-Core aligns with key international standards under active development:
At coRAN Labs, our Post Quantum upgrade strategy for Aether SD-Core aligns with key international standards under active development:
- NIST FIPS 203, 204, 205
Standardization of ML-KEM, ML-DSA, and SLH-DSA as the foundational PQ primitives for encryption/key encapsulation and digital signatures.
- IETF drafts for migrating security protocols
- PQ-TLS 1.3 – Internet-Draft efforts extend traditional protocols (TLS, IPsec, PKIX, etc.) with PQ-KEM and PQ signature schemes. These drafts define identifiers, implementation guidance, and interoperability considerations.
- X-Wing KEM (draft-connolly-cfrg-xwing-kem-09) – Introduces hybrid KEMs such as X25519MLKEM768, providing stronger protection against binding attacks and improved performance over naive combinations.
- PQ-X.509 Certificates (draft-ietf-lamps-pq-composite-sigs-13) – Defines composite signature mechanisms that combine a post-quantum signature algorithm with a classical algorithm (e.g., RSASSA-PSS, ECDSA, Ed448, EdDSA), enabling a gradual transition to PQC while preserving confidence in well-understood classical schemes.
- PQ-TLS 1.3 – Internet-Draft efforts extend traditional protocols (TLS, IPsec, PKIX, etc.) with PQ-KEM and PQ signature schemes. These drafts define identifiers, implementation guidance, and interoperability considerations.
- GSMA PQTN, 3GPP SA3
- GSMA PQ.03, PQ.05 and related whitepapers provide a roadmap for PQ migration in telecom, covering risks, upgrade paths, challenges, and use cases across 5GC and roaming interfaces.
- 3GPP SA3 is actively evaluating PQC integration into the 5G Security Framework, focusing on access and core interfaces, authentication, and key management ensuring that PQ adoption does not disrupt service continuity.
- GSMA PQ.03, PQ.05 and related whitepapers provide a roadmap for PQ migration in telecom, covering risks, upgrade paths, challenges, and use cases across 5GC and roaming interfaces.
By aligning QORE’s PQ-Aether SD-Core implementation with these standards, we ensure:
- Interoperability
- Forward compatibility
- Crytographic agility
enabling operators to transiion gradually without disrupting existing deployments.
Why Aether SD-Core is the Right Platform for QORE
In a landscape dominated by closed ecosystems, open platforms are essential for transparent innovation, security research, and rapid standard adoption. Aether, as an open source 5G platform under the Linux Foundation, embodies this philosophy.
Our decision at coRAN Labs to build QORE on Aether SD-Core is driven by several strengths:
- 3GPP Compliance
Aether’s adherence to 3GPP specifications ensures interoperability and a standards-aligned foundation for future-proof deployments. - Modular Design
Componentized network functions make it straightforward to integrate custom implementtions such as PQ-capable O Auth server and PQ-aware SBI endpoints. - Cloud-Native Architecture
Aether’s cloud-native design enables highly scalable, observable, and automatable deployments critical for modern DevSecOps workflows and PQ rollouts at scale. - End-to-End 5G Core
Aether SD-Core offers a comprehensive 5G core solution that can be readily deployed in private and enterprise 5G use cases, making it an ideal testbed for PQ upgrades. - Community-Driven Development
Aether is backed by an active community that prioritizes technical excellence, transparency, and shared learning making it a perfect ecosystem for pioneering quantum-safe enhancements.
Post-Quantum Migration of Aether SD-Core
Building on Aether’s cloud-native platform, we performed a full Post-Quantum migration of the Service-Based Interfaces (SBI) of SD-Core. Our objective was to keep the same application behavior and performance characteristics while augmenting the security posture with quantum resilience.
Key aspects of the migration include:
- Upgrades applied at individual Network Functions (NFs), focusing on SBI server endpoints and their HTTP APIs.
- For OAuth 2.0, we target the JWT and OpenAPI libraries with necessary modifications in NF components.
- The Golang toolchain was rebased and patched to natively support PQ primitives:
- PQ signature schemes (ML-DSA and hybrids)
- PQ KEMs (ML-KEM and hybrids)
- PQ-aware X.509 certificate parsing and validation
We used cryptographic libraries such as Cloudflare’s CIRCL to obtain robust, standards-aligned implementations of PQ primitives.
Within SD-Core, we focused on three main migration tracks:
- TLS 1.3 to PQ-TLS 1.3
- X.509 to PQ X.509
- OAuth 2.0 to PQ-OAuth 2.0
About coRAN Labs
coRAN Labs (CRL) is focused on building secure, open, and interoperable RAN and Core solutions for next-generation telecom networks. Through projects like QORE (Quantum-Secure 5G Core) and Q-RAN, we collaborate with open-source communities such as Aether to provide practical reference architectures and implementations for quantum-safe telecom migration.
If you are an operator, integrator, or researcher interested in trialing or contributing to QORE on Aether SD-Core or anyCORE, we’d be delighted to collaborate.











 “The demo setup with desktop PCs running a disaggregated 5G private mobile network. Our live installation also showcased the ability to deploy the 5G PMN as disaggregated components. This included the control and user plane separation (CUPS) capability of Charmed Aether SD-Core.”
“The demo setup with desktop PCs running a disaggregated 5G private mobile network. Our live installation also showcased the ability to deploy the 5G PMN as disaggregated components. This included the control and user plane separation (CUPS) capability of Charmed Aether SD-Core.”